Security Vulnerabilities Associated with Inventory
FlexNet Code Insight uses data from the National Vulnerability Database (NVD) and other advisories such as RubySec to report security vulnerabilities associated with your inventory items. The vulnerabilities information from these sources is used to create vulnerability rankings and alerts.
The Vulnerabilities bar graph shows the current security-vulnerability counts by severity level for a given inventory item listed in Analysis Workbench or on the Project Inventory tab:

The color-coded segments represent the different severity levels as follows:
|
•
|
Red—High severity (CVSS 7.0 - 10.0) |
|
•
|
Gold—Medium severity (CVSS 4.0 - 6.9) |
|
•
|
Yellow—Low severity (CVSS 0.1 - 3.9) |
|
•
|
Gray—Unknown severity (N/A) |
For example, the Vulnerabilities graph above indicates 50 vulnerabilities of high severity, 33 of medium severity, 1 of low severity, and 80 of unknown severity.
The following procedure explains how to use this graph to obtain details about the security vulnerabilities associated with the inventory item.
To view security vulnerabilities for an inventory item, do the following:
|
1.
|
For a specific inventory item, click any of the Vulnerabilities counts (red, orange, yellow, or gray) in the graph. The Security Vulnerabilities dialog appears. |
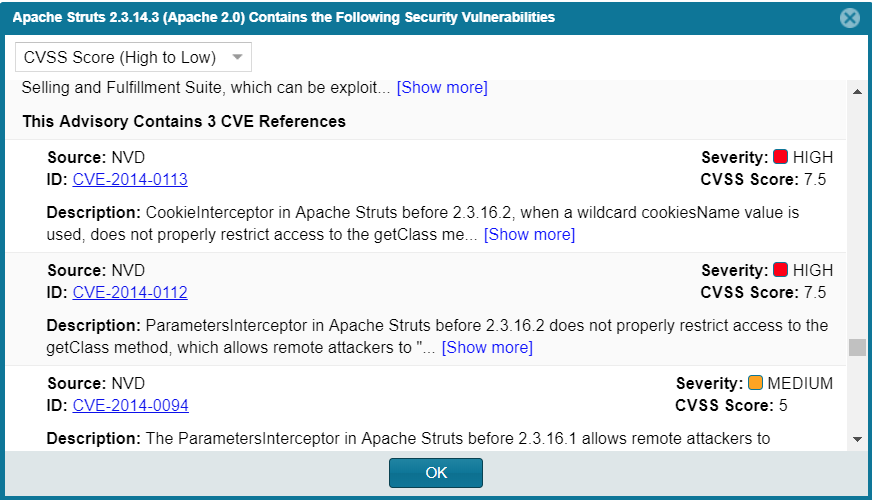
Note the following details about the Security Vulnerabilities list:
|
•
|
Each entry identifies a specific security vulnerability associated with the selected inventory item. A vulnerability can be reported by the National Vulnerability Database (NVD) in the form of a CVE (Common Vulnerabilities and Exposures), by Secunia Research in the form an SA (Secunia Advisory), or by other research organizations using their own vulnerability ID formats. In some cases, CVEs will be referenced by one or more advisories. A given entry includes the ID for the vulnerability or advisory, as well as its source (such as NVD or Secunia), severity, CVSS (Common Vulnerability Scoring System) score, and description. |
|
•
|
In some cases, the vulnerability or advisory CVSS score is unknown because it has not been scored by the supplier. These vulnerabilities are reported by Code Insight with a CVSS score of N/A and a severity of UNKNOWN. |
Note • Your feedback is welcome in how to handle the severity and scoring of currently unscored vulnerabilities. The FlexNet Code Insight team will do its best to incorporate the results of this feedback into the Code Insight vulnerability database. Contact FlexNet Code Insight Support (see Contacting Us).
|
•
|
You can click the vulnerability or advisory link (if available) to further investigate the vulnerability and determine the severity and score of the vulnerability as it applies to your project. |
|
•
|
The Security Vulnerabilities list represents vulnerabilities and advisories in a hierarchical fashion, with Secunia and other advisories at the top level, and CVEs at the secondary level of the hierarchy. This behavior is in place because advisories are often well-researched and provide additional information above what is provided by the NVD. CVEs that are not referenced by any advisories also appear at the top-level of the hierarchy. The hierarchy view is two levels deep. |
|
•
|
A CVE that is referenced by multiple advisories for the given inventory item is shown in the secondary list under each of the advisory entries. However, the vulnerability itself will count only once in the Vulnerabilities count on Inventory Details tab. |
|
•
|
All top-level entries (CVEs and advisories) are sorted by CVSS score. Similarly, CVE vulnerabilities in a secondary list under a top-level advisory entry are sorted by CVSS score within the secondary list. |
|
•
|
The Security Vulnerabilities list shows only explicit CVE vulnerabilities, Secunia advisories, or other advisories (that is, those directly mapped to the component version identified by the inventory item) and lists them in their proper hierarchical position. |
|
2.
|
(Optional) Click the hyper-linked CVE in an entry to view the vulnerability details found on the NVD or other website. Accessing these links is recommended if conducting deeper research as it shows referenced CVEs (those that are not explicitly mapped to the component version but can be indirectly related). |
|
3.
|
When you have finished viewing the reported vulnerabilities, click OK to close the dialog. |
Open topic with navigation


