Suppressing a Security Vulnerability
Code Insight 2021 R3
The following procedure is used to suppress a security vulnerability for one or more (or all) versions of an OSS or third-party component associated with your inventory.
To suppress a security vulnerability, do the following:
| 1. | Locate the Vulnerabilities bar graph within the context of a given inventory item or component version. (See Impact of Suppressing a Security Vulnerability for the locations of this graph.) |
The graph is displayed only if vulnerabilities exist for the inventory item or component version.
| 2. | Click anywhere on the Vulnerabilities bar graph. |
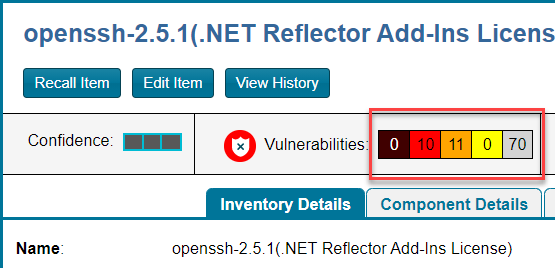
The Security Vulnerabilities window is displayed. (This example uses the CVSS v3.x scoring system.)

| 3. | Locate the security vulnerability that you want to suppress, and click the Suppress button next it ID field. |
The Suppress Vulnerability window is displayed.
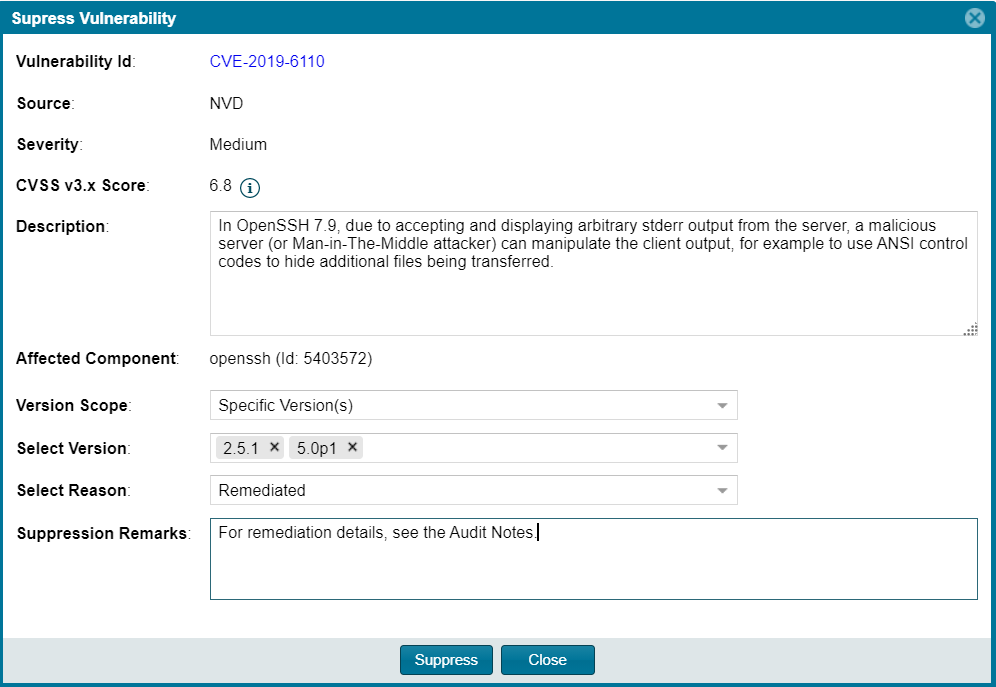
| 4. | Complete all editable fields on the window to define the vulnerability suppression. For a description of these fields, see Suppress Vulnerability Window. |
| 5. | Click Suppress. Then click OK in the pop-up to acknowledge that the vulnerability has been suppressed for the specified component versions. |
If other vulnerabilities exist for the inventory item, you are returned to the Security Vulnerabilities window. The suppressed vulnerability should no longer be visible in the window (if you suppressed the vulnerability for the component version of the current inventory item).
If this vulnerability is the only one for the inventory item, you are returned to the previous context from which you opened the Security Vulnerabilities window (for example, the Inventory Details tab or the Lookup Component window). The Vulnerabilities bar graph count should be reduced in the specific severity segment associated with the suppressed vulnerability (if you suppressed the vulnerability for the component version of the current inventory item).