Examining Security Vulnerability Details
The following procedure explains how to use the Vulnerabilities bar graph to obtain details about the security vulnerabilities associated with a specific inventory item or component version.
The Vulnerabilities bar graph is displayed for any of the following entities if the entity is associated with security vulnerabilities:
|
•
|
A specific inventory item in the Analysis Workbench or in Project Inventory |
|
•
|
A component version in an inventory item’s Lookup Component window |
|
•
|
A component version in the Global Component & License Lookup window |
To view security vulnerabilities for an inventory item, do the following:
|
1.
|
Click anywhere on the Vulnerabilities bar graph. |
(The graph is displayed only if vulnerabilities exist for the inventory item or component version.)
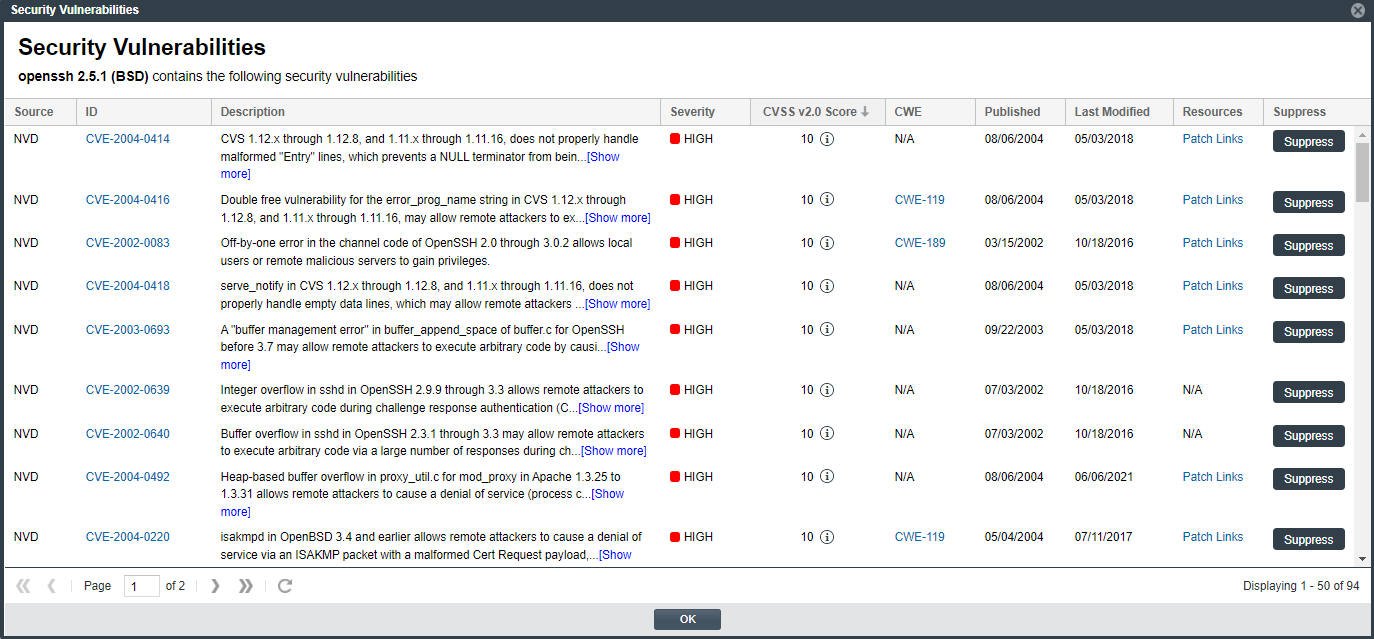
The Security Vulnerabilities window is displayed. (This example uses the CVSS v3.x scoring system.)
Note:When a security vulnerability is suppressed for the component version associated with the current inventory item, the vulnerability is not visible on the Securities Vulnerabilities window, nor is it reflected in the counts on Vulnerabilities bar graph.
|
2.
|
Examine the vulnerabilities in the Security Vulnerabilities list. For a description of the details shown for each vulnerability entry, see Security Vulnerabilities Window. Note the following about the list itself: |
|
•
|
Each entry in the Security Vulnerabilities list identifies a specific security vulnerability directly associated with the selected inventory item. A vulnerability can be reported by the NVD (National Vulnerability Database) as a CVE (Common Vulnerabilities and Exposures) or by a research organization such as Secunia, Debian, or others. (Such organizations publish well-researched security advisories about CVEs that can include information not found in the NVD descriptions.) |
|
•
|
By default, the list is sorted on the CVSS <version> Score column in descending order. |
|
•
|
If a CVE is both published by the NVD and referenced in one or more advisories, the vulnerability is counted separately for each location. For example, a CVE that is published by the NVD and referenced in two advisories will have a count of 3 reflected in the vulnerability totals (as displayed on the project dashboards and Vulnerabilities bar graphs in the Web UI, as well as shown in API responses and the Project and Audit reports). |
|
•
|
In cases where the vulnerability score is unknown (and reported as N/A in the list), the severity level of the vulnerability is reported as None or Unknown. (For more information about the vulnerability score and severity, see Security Vulnerabilities Window.) |
Note:Your feedback is welcome on how Code Insight should handle the severity and scoring of currently unscored vulnerabilities. The Code Insight team will do its best to incorporate the results of this feedback into the Code Insight vulnerability database. Contact Revenera Support with your suggestions.
|
3.
|
When you have finished with the Security Vulnerabilities window, click OK to close the window. |

