Suppressing Security Vulnerabilities
The System Administrator can suppress a security vulnerability at the Code Insight system level for one or more (or all) component versions associated with the vulnerability. The following provides more details:
| • | Effects of Suppressing a Security Vulnerability |
| • | Suppressing a Security Vulnerability |
Effects of Suppressing a Security Vulnerability
The suppression of a security vulnerability has an impact on your Code Insight system. That is, once a vulnerability is suppressed for a specific component version, it is no longer counted in vulnerability totals or is visibly listed at the project, inventory, and component-version levels. The count reduction is evident on the project dashboards and on the Vulnerabilities bar graphs in the Web UI, as well as in subsequently generated API responses and reports (Project and Audit). Likewise, the actual vulnerability is no longer visible in the list of vulnerabilities on the Security Vulnerabilities window (which is opened when you click a Vulnerabilities bar graph) or in API responses or reports.
Note:The Vulnerabilities bar graph in the UI is shown on the Inventory view, in the Lookup Component window for a specific component version, and in Inventory Details for a given inventory item (both on the Project Inventory tab and in the Analysis Workbench).
The following describes the impact that a security vulnerability suppressed for a specific component version has on other features of Code Insight:
| • | Advanced Search on the Project Inventory tab and Inventory View—When an inventory search is based the vulnerability name or severity, the results do not show inventory items that are related to the suppressed vulnerability. |
| • | Alerts—Any open alerts for the suppressed vulnerability are automatically closed, and the open and closed alert counts are adjusted on the Project Inventory tab, in the Analysis Workbench, and on the Inventory view. |
| • | Policies—Once a security vulnerability is suppressed, no changes are initially propagated to those review policies that are based on vulnerabilities. However, each time one of these policies is triggered thereafter (that is, when an inventory item is published), the policy ignores the suppressed vulnerability when determining whether to automatically approve or reject the published inventory item. |
Additionally, a change in policy due to the suppression of a vulnerability does not change the existing approval/rejection status of a published inventory item unless the item is manually recalled and then republished.
| • | Subsequent scans and rescans—Once a vulnerability is suppressed, it is not reflected in the results of subsequent rescans and initial scans, whether incremental or full. |
Suppressing a Security Vulnerability
The following procedure is used to suppress a security vulnerability for one or more (or all) versions of an OSS or third-party component associated with your inventory.
Note:A System Administrator can also suppress a security vulnerability using the Suppress vulnerability REST API. For more information about this API, see the Code Insight Swagger documentation, available from the Help > REST API Guide option on the Code Insight menu. (To access this menu, click the  icon in the upper right corner of the Code Insight web page.)
icon in the upper right corner of the Code Insight web page.)
To suppress a security vulnerability, do the following:
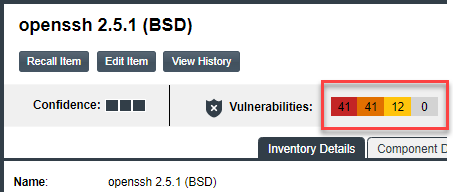
| 1. | Locate the Vulnerabilities bar graph within the context of a given inventory item or component version. |
Note:The Vulnerabilities bar graph in the UI is shown on the Inventory view, in the Lookup Component window for a specific component version, and in Inventory Details for a given inventory item (both on the Project Inventory tab and in the Analysis Workbench).
The graph is displayed only if vulnerabilities exist for the inventory item or component version.
| 2. | Click anywhere on the Vulnerabilities bar graph. |
The Security Vulnerabilities window is displayed. (This example uses the CVSS v3.x scoring system.)
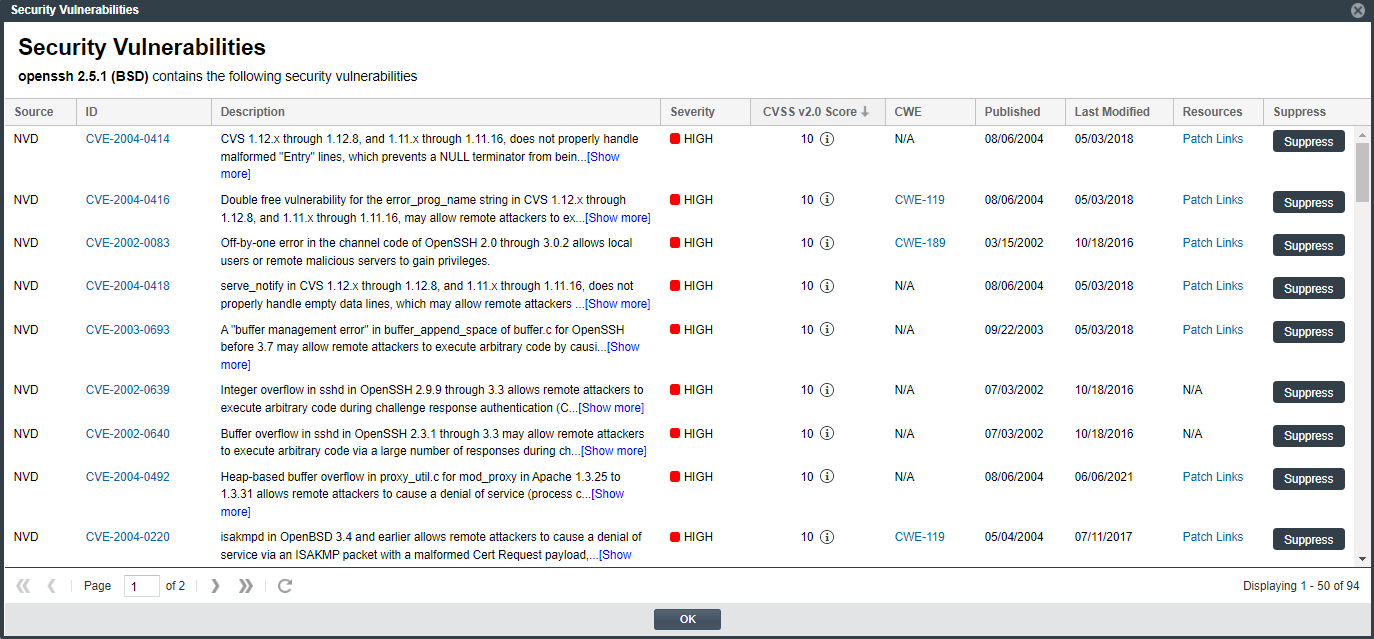
| 3. | Locate the security vulnerability that you want to suppress, and click the Suppress button next its ID field. |
The Suppress Vulnerability window is displayed.
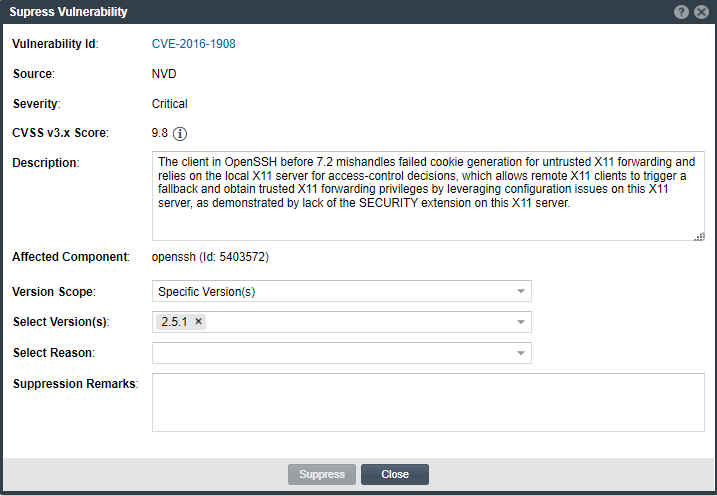
| 4. | Complete all editable fields on the window to define the vulnerability suppression. For a description of these fields, see Suppress Vulnerability Window. |
| 5. | Click Suppress. Then click OK in the pop-up to acknowledge that the vulnerability has been successfully suppressed for the specified component versions. |
If other vulnerabilities exist for the inventory item, you are returned to the Security Vulnerabilities window. The suppressed vulnerability should no longer be visible in the window (if you suppressed the vulnerability for the component version of the current inventory item).
If this vulnerability is the only one for the inventory item, you are returned to the previous context from which you opened the Security Vulnerabilities window (for example, the Inventory Details tab or the Lookup Component window). The Vulnerabilities bar graph count should be reduced in the specific severity segment associated with the suppressed vulnerability (if you suppressed the vulnerability for the component version of the current inventory item).