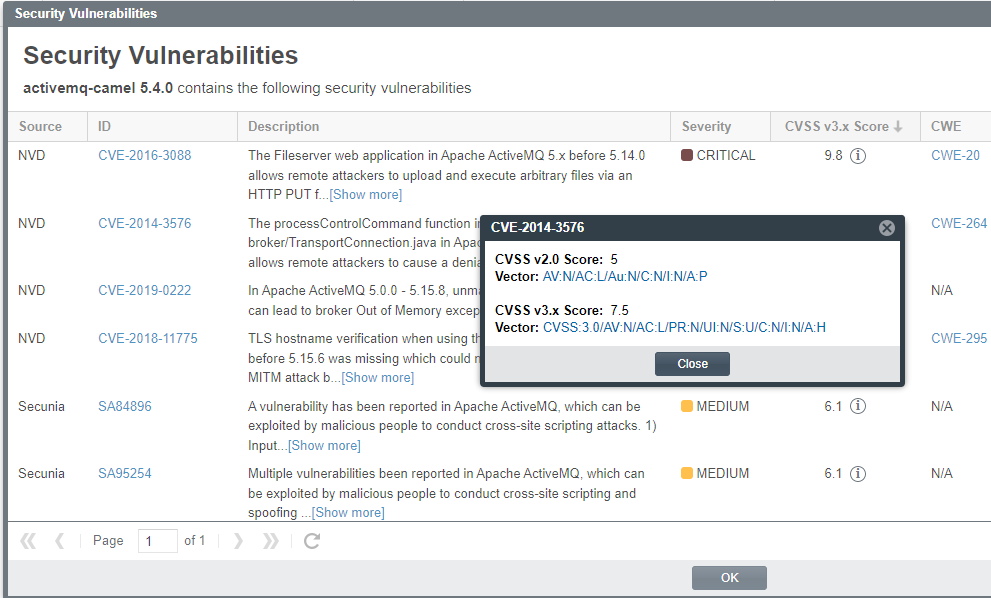
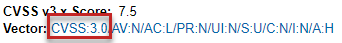Security Vulnerabilities Window
The Security Vulnerabilities window lists all the security vulnerabilities currently associated with a specific inventory item or component version and provides details and lookups for each vulnerability. You access this window by clicking the Vulnerabilities bar graph displayed for any of the following entities—if that entity currently has security vulnerabilities:
| • | A specific inventory item in the Analysis Workbench or in Project Inventory |
| • | A specific inventory item listed on the Inventory view |
| • | A component version in an inventory item’s Lookup Component window |
| • | A component version in the Global Component & License Lookup window |
For more information about examining the vulnerabilities on this window, see Examining Security Vulnerability Details.
The following describes the properties shown for each security vulnerability listed in the Security Vulnerabilities window. These properties are not editable.
By default, the list of vulnerabilities on this window are sorted on the CVSS <version> Score column in descending order.
|
Property |
Description |
|||||||||
|
Source |
The security database system or research organization that has reported the security vulnerability (for example, NVD, Secunia, or another research organization). |
|||||||||
|
ID |
The ID of the security vulnerability in the format of the advisory organization that reported it:
Optionally, you can click the hyperlinked CVE ID to open its external third-party web page on a separate tab. The web page can provide referenced CVEs (those not explicitly mapped to the component version but indirectly related to it) and other useful information for researching the vulnerability. The list is sortable on this column. See Grid Control for details. |
|||||||||
|
Description |
A description of the security vulnerability pulled from the source. A More/Less link enables you to view the full description and then collapse it as needed. |
|||||||||
|
Severity |
The severity of the vulnerability (CRITICAL, HIGH, LOW, or other). The level of severity depends on the scoring system used and the vulnerability’s actual CVSS score. For details about the relationship between severity levels and CVSS scoring systems, see Understanding Severity Levels for Security Vulnerabilities. |
|||||||||
|
The vulnerability’s CVSSv3 (Common Vulnerability Scoring System) score. In some cases, the advisory CVSS score (or other type of vulnerability score) is unknown for a vulnerability because it has not been provided by the supplier. Code Insight reports the score for such a vulnerability as If you click the
The associated Vector value for a v3.x vulnerability has the specific score version—3.0 or 3.1—embedded in the value.
The Vector value is available only if the vulnerability is found in the NVD. (Otherwise, the Vector field shows N/A.) This hyperlinked value for this field is a compressed textual representation of the values used to derive the score. When you click the link, the appropriate NVD Common Vulnerability Scoring System Calculator is opened, showing you the environmental and temporal factors that determined the score. You can use the calculator to tweak these factors as necessary to calculate another score that is more realistic for your software product. (Instructions are provided with the calculator.) This adjusted score can then be used internally to direct your review and remediation processes. The list is sortable on this column. See Grid Control for details. |
||||||||||
|
CWE |
The vulnerability’s CWE (Common Weakness Enumeration) type. Optionally, you can click the hyperlinked ID to open the CWE web page describing this type. (CWE types are developed by a community of national cyber-security organizations.) |
|||||||||
|
EPSS Score |
The vulnerability’s EPSS (Exploit Prediction Scoring System) score, depicting its likelihood of exploitation within the next 30 days. Scores range from 0 to 1 (or 0% to 100%). The higher the score, the greater likelihood of exploitation. For more information, refer to EPSS external website. |
|||||||||
|
EPSS Percentile |
The vulnerability’s EPSS (Exploit Prediction Scoring System) percentile, representing its relative measure of threat compared to all other CVE vulnerabilities. The higher the percentile, the higher the threat risk compared to other vulnerabilities. For more information, refer to EPSS external website. |
|||||||||
|
Published |
The date on which the vulnerability was originally published, as retrieved from its source (NVD, Secunia, or another advisory).1 |
|||||||||
|
Last modified |
The date on which the vulnerability was last revised, as retrieved from its source (NVD, Secunia, or another advisory). If vulnerability has never been revised, the field displays the vulnerability’s published date.1 |
|||||||||
|
Resources |
If the Patches link displayed, click it to open a pop-up window that lists the patches currently available to fix the vulnerability. From the popup, you can click the hyperlinked URL for any patch listed to open its external third-party web page on a separate tab. The web page provides information about the patch and how to execute it. If no patches are available for the vulnerability, N/A is displayed in this column. |
|||||||||
|
Analysis |
Note:This button is visible for each vulnerability only when the current window is accessed by clicking the Vulnerabilities bar graph for an inventory item in the Analysis Workbench or on the Project Inventory tab. Click this button to open the Analyze or Suppress Vulnerability Window, enabling you to do the following:
Alternatively, a System Administrator can choose to suppress the vulnerability at the global level. See Suppressing or Unsuppressing a Security Vulnerability at the Global Level.
|
|||||||||
|
Suppress |
Note:This button is visible for each vulnerability only if you are a System Administrator and if the current window was accessed by clicking the Vulnerabilities bar graph:
Click this button to open the Suppress Vulnerability Window, which enables you to suppress the vulnerability at the global level. For more information, see Suppressing or Unsuppressing a Security Vulnerability at the Global Level. |
1 If you have migrated from a pre-2021 R3 Code Insight release to the current release, you must run an Electronic Update to obtain the latest date information.
Do the following to manage the grid.
| • | Control the column presentation: |
| • | Click the up  (or down arrow) in the ID or CVSS <version> Score column header (or select the appropriate sorting order from the header’s dropdown menu) to sort the vulnerability list in ascending or descending order. (or down arrow) in the ID or CVSS <version> Score column header (or select the appropriate sorting order from the header’s dropdown menu) to sort the vulnerability list in ascending or descending order. |
By default, the list grid is sorted on the CVSS <version> Score column in descending order.
| • | Click the dropdown menu in any column header to select the columns you want to display or hide in the grid. |
| • | The grid is paginated with each page having 50 records. Use the navigation icons at the bottom of the grid to move between next or previous pages or to a specific page. |