Reviewing Vulnerabilities
FlexNet Code Insight 6.13.2
This chapter provides the procedure for doing a security scan by reviewing vulnerabilities.
When an inventory item is scheduled for a full review by a project owner and it has been through a review and reconciliation process to determine its IP compliance state, a secondary review by the security analyst assigned to the project must occur if the inventory item contains associated security vulnerabilities.
To review vulnerabilities, do the following:
|
1.
|
Log into FlexNet Code Insight as a Security Analyst. A security analyst is a user with a project participant role who is assigned as a security analyst for a given project. |
|
2.
|
Click the My Projects button, and a list of projects opens. |
|
3.
|
Click the magnifying glass icon next to the project you want to review. The Project page opens. |
|
4.
|
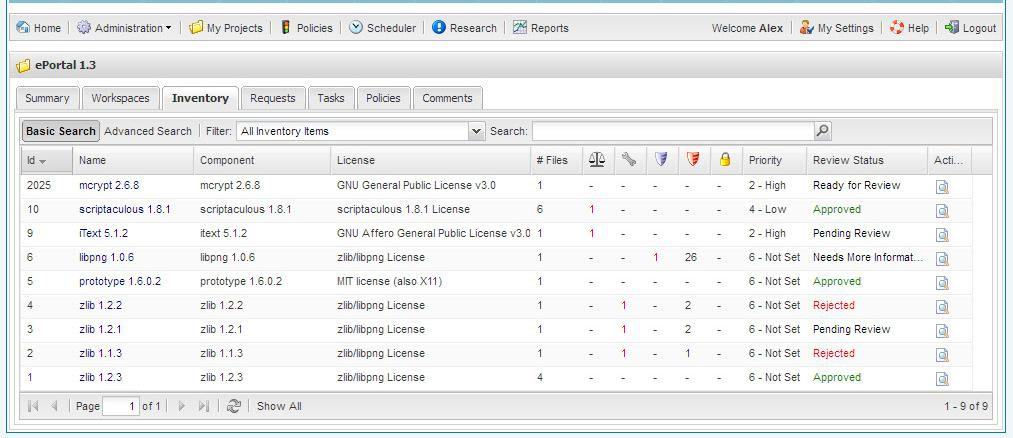
Click the Inventory tab. |
|
5.
|
Select an inventory item, and click the associated magnifying glass icon. The Inventory details page appears. |
|
6.
|
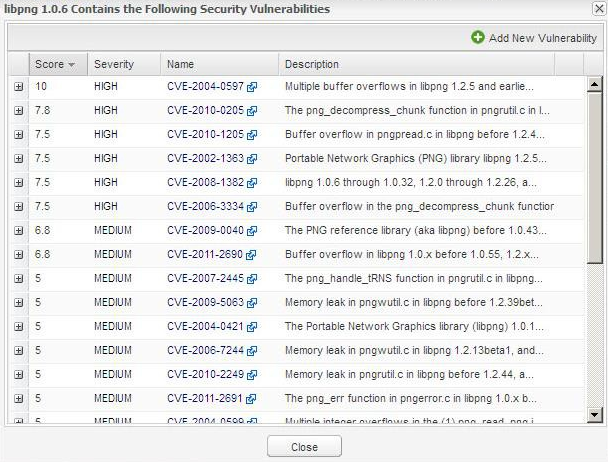
In the Components line, click the Vulnerability Shield icon ( ) in the top left corner of the Inventory Details page to view vulnerabilities details. The Contains the Following Security Vulnerabilities dialog appears: ) in the top left corner of the Inventory Details page to view vulnerabilities details. The Contains the Following Security Vulnerabilities dialog appears: |
|
7.
|
To expand the descriptions, click the Plus icon to the left of the Score column. |
|
9.
|
From the Change Inventory Status pull-down menu, select Approve, Reject or Schedule Full Review of the inventory item when you have completed reviewing the associated vulnerabilities. |
Open topic with navigation


 ) in the top left corner of the Inventory Details page to view vulnerabilities details. The Contains the Following Security Vulnerabilities dialog appears:
) in the top left corner of the Inventory Details page to view vulnerabilities details. The Contains the Following Security Vulnerabilities dialog appears: